[ad_1]
As we head closer to the fall release of new versions of Apple’s operating system for iPhone, iPad and Mac, there is more confirmation about the exact contours of how the data privacy and security features will be expectedly strengthened. The three OSes — iOS 16, iPadOS 16 and macOS Ventura — will get something called a Lockdown Mode, which includes an extensive set of features, to ward off sophisticated cyberattacks and digital threats. The thing is, you’ll likely not get this exact feature.
Apple says this mode (option or setting), will be available to a “very small number of users who face grave, targeted threats to their digital security”. This demographic will likely be well-known personalities who’ve been previously targeted using sophisticated malware including Pegasus (this is developed by Israeli firm NSO Group and was in the news recently, including in India), as well as those who may be potentially targeted.
The criteria for being accepted into this club will likely never be completely revealed, but some possible at-risk professions include politicians, activists, journalists, and anyone a state may consider a dissident or threat. Apple minces no words while pointing out governments in different countries sponsor these sophisticated and targeted digital attacks on individuals.
Also Read:Alder Lake-HX — Intel’s powerful response to Apple M2 chips for laptop CPUs
“Lockdown Mode offers an extreme, optional level of security for the very few users who, because of who they are or what they do, may be personally targeted by some of the most sophisticated digital threats, such as those from NSO Group and other private companies developing state-sponsored mercenary spyware,” the company says in a statement.
Nonetheless, what will the Lockdown Mode entail?
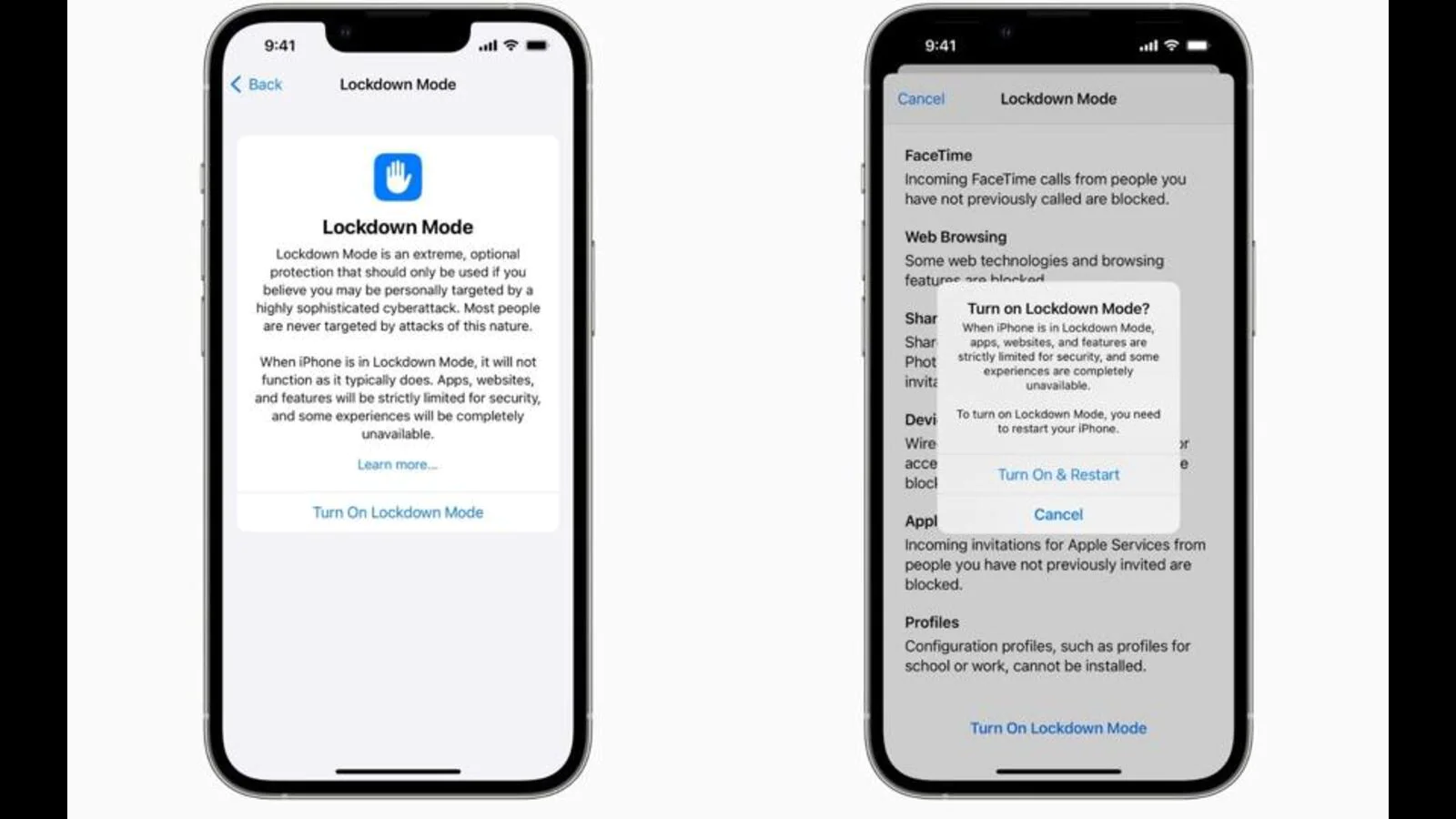
This is an optional and multi-layered set of options that’ll strengthen the existing shields that monitor all the data that’s coming in and going out from an iPhone, iPad, or Mac. For instance, in Messages, attachments other than images will be blocked and previews of links shared in chats will be disabled. Complex web technologies, such as the just-in-time (JIT) JavaScript compilation, can be disabled with the user getting the option to exclude a trusted site from Lockdown Mode.
Any new invitations or service requests for FaceTime calls, Message groups and other communication methods (these are limited to Apple’s own services for the moment) will be blocked if the person sending these requests hasn’t previously received a call or a request from the user of the iPhone, iPad or Mac. Also, attempts to connect a wired accessory or network to an iPhone will be blocked. “Configuration profiles cannot be installed, and the device cannot enroll into mobile device management (MDM), while Lockdown Mode is turned on,” Apple confirms.
Targeted attacks for surveillance using spyware often include extracting and monitoring contents on the infected device (phones, tablets and computers), accessing documents and media including photos, the ability to active any of the cameras on the phone without the user knowing about it and also accessing the microphone to listen in on conversations. Each spyware has its own strong points, depending on what it is being deployed for.
In November, Apple sued NSO group after a global fracas about the Pegasus spyware that was used as a weapon for state-sponsored surveillance (though the debate is still on in the matter) in many countries. Personalities using iPhones and Android phones were targeted for monitoring. Apple had also quickly moved to patch the vulnerability that allowed the spyware a route to be installed on unsuspecting users’ iPhones. Citizen Lab, a research group at the University of Toronto, had first identified the exploit in iOS.
“State-sponsored actors like the NSO Group spend millions of dollars on sophisticated surveillance technologies without effective accountability. That needs to change,” said Craig Federighi, Apple’s senior vice president of Software Engineering, had said at the time.
Spyware attacks are a global phenomenon.
Around the time when Apple sued NSO Group, a report by security firm Sophos indicated that new variants of spyware being used by a threat actor group called C-23, continue to target individuals based in the Middle East. “The new variants appear in the form of an app that purports to install updates on the target’s phone, with names that include App Updates, System Apps Updates, or Android Update Intelligence,” said Pankaj Kohli, researcher at SophosLabs, at the time.
Researchers at mobile security form Zimperium had noted in a new report that a spyware campaign is targeting Android phone users in South Korea. The spyware, called PhoneSpy, had been discovered in 23 popular Android apps distributed on stores other than the Google Play Store. It can enable a user’s phone camera to take photos or record videos, as well as access data and microphone.
In April, Citizen Lab researchers revealed that as many as 65 activists, politicians, and civil society groups were targeted using Pegasus in Catalonia, an autonomous region in Spain.
[ad_2]
Source link